In today’s interconnected digital world, users often need to grant applications access to their data without sharing their passwords. This is where OAuth (Open Authorization) comes in—a secure and standardized protocol that allows third-party applications to access user resources on their behalf. Whether it’s logging in with Google, accessing your calendar, or connecting to a cloud service, OAuth makes it possible.
In this blog, we’ll break down the four OAuth flows, explain their differences, and help you understand when to use each one. We’ll also explore how Microsoft Entra ID (formerly Azure Active Directory) implements OAuth and why it’s a powerful choice for securing your applications.
What is OAuth?
OAuth is an open standard for access delegation. It allows users to grant limited access to their resources (like files, emails, or calendars) on one service to another service, without exposing their credentials. Instead of sharing passwords, OAuth uses access tokens to authorize requests.
Think of OAuth as a valet key for your car. You give the valet a key that lets them drive your car, but it doesn’t give them access to your glovebox or trunk. Similarly, OAuth grants applications limited access to your data without exposing your full credentials.
The Four OAuth Flows
OAuth provides different flows (or grant types) to accommodate various use cases. Let’s break them down with simple explanations and examples.
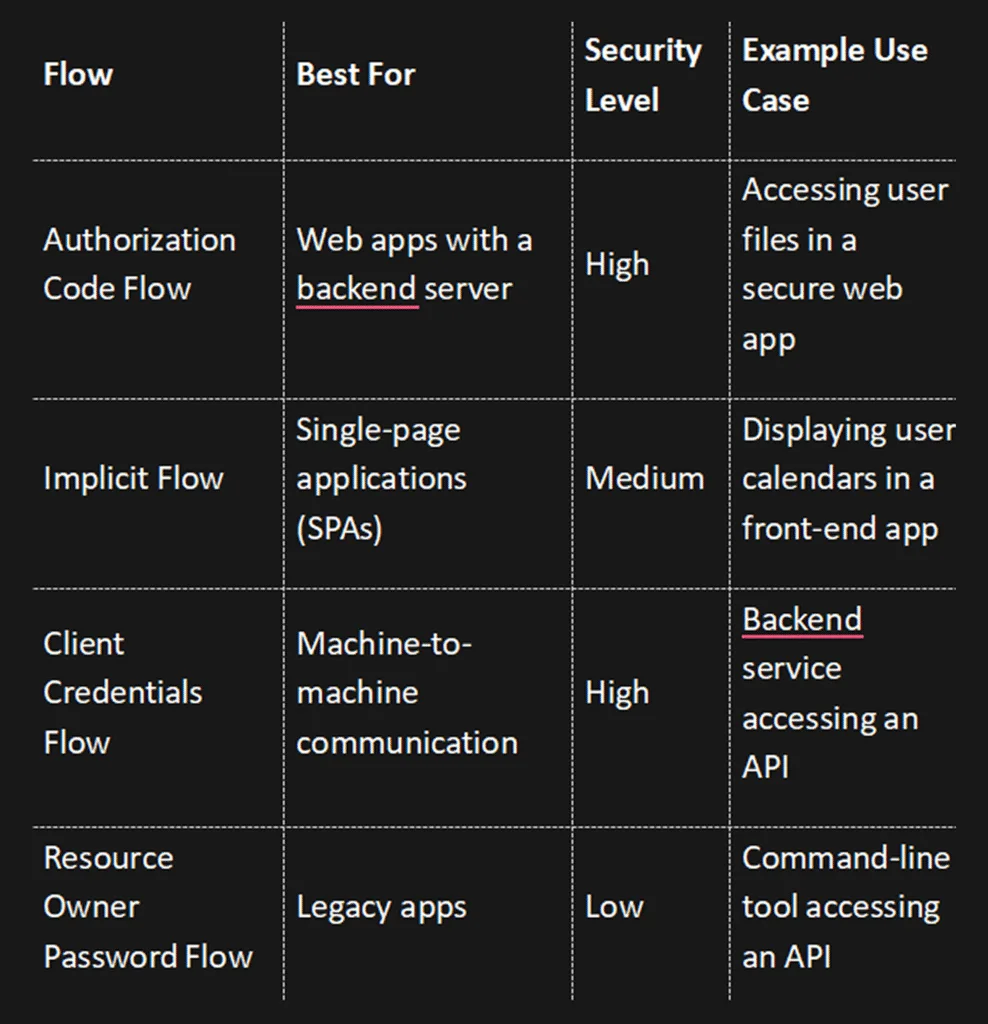
1. Authorization Code Flow
How it works:
- The user logs in and grants permission to the application.
- The application receives an authorization code.
- The application exchanges the authorization code for an access token by authenticating itself with the authorization server.
Use Case:
- Web applications with a backend server.
- Example: A web app that needs access to a user’s Google Drive files.
Why it’s secure:
The access token is never exposed to the user’s browser, reducing the risk of interception.
2. Implicit Flow
How it works:
- The user logs in and grants permission.
- The application directly receives an access token from the authorization server.
Use Case:
- Single-page applications (SPAs) like React or Angular apps.
-
Example: A front-end app that displays a user’s calendar events.
Why it’s less secure:
The access token is exposed in the browser, making it vulnerable to interception. For this reason, it’s being phased out in favor of the Authorization Code Flow with PKCE.
3. Client Credentials Flow
How it works:
- The application authenticates itself with the authorization server using its client ID and client secret.
- The authorization server issues an access token.
Use Case:
- Machine-to-machine communication.
-
Example: A backend service accessing an API to process data.
Why it’s secure:
4. Resource Owner Password Credentials (ROPC) Flow
How it works:
- The user provides their username and password directly to the application.
- The application sends these credentials to the authorization server to obtain an access token.
Use Case:
- Legacy applications where other flows are not feasible.
-
Example: A command-line tool that needs quick access to an API.
Why it’s risky:
Comparison of OAuth Flows
How Microsoft Entra ID Implements OAuth
Microsoft Entra ID (formerly Azure Active Directory) is Microsoft’s cloud-based identity and access management service. It fully supports OAuth 2.0 and provides seamless integration with applications, APIs, and services.
Here’s how Microsoft Entra ID implements OAuth:
- Authorization Server: Microsoft Entra ID acts as the authorization server, issuing
tokens to applications after successful authentication. - Access Tokens: Microsoft Entra ID generates secure access tokens that applications
use to access resources like Microsoft Graph, Azure APIs, or custom APIs. - PKCE Support: Microsoft Entra ID supports Proof Key for Code Exchange (PKCE),
enhancing the security of the Authorization Code Flow for SPAs. - Multi-Tenant Support: Microsoft Entra ID allows applications to authenticate users
from multiple organizations, making it ideal for SaaS applications.
Example Use Case with Microsoft Entra ID:
When to Use Microsoft Entra ID for OAuth
Microsoft Entra ID is a great choice if:
- You’re building applications that need to integrate with Microsoft services like
Microsoft 365 or Azure APIs. - You need enterprise-grade security features like conditional access, multi-factor
authentication, and token encryption. - You want a scalable, reliable identity provider for your applications.
If you’re unsure how to implement OAuth with Microsoft Entra ID or need help configuring your application, we’re here to assist. With our expertise, we can ensure your OAuth implementation is secure, efficient, and tailored to your needs.
Conclusion
OAuth is a powerful protocol that enables secure access delegation for applications. By understanding the four OAuth flows—Authorization Code, Implicit, Client Credentials, and Resource Owner Password—you can choose the right flow for your use case. Platforms like Microsoft Entra ID make implementing OAuth seamless, especially for applications that require enterprise-grade security and scalability.
If you’re ready to implement OAuth in your application but need guidance, feel free to reach out to us. Whether it’s integrating with Microsoft Entra ID or securing your APIs, we’re here to help you every step of the way. Let’s make your application secure and future-ready!
